Battling the New Backdoor
Whenever technology becomes more sophisticated, so does malware—malicious software designed to cause harm to computers, computer networks, or their users.
Cybersecurity experts are always trying to foresee the next threat, and with the rise of artificial intelligence (AI) and machine learning (ML), those threats are becoming incredibly intricate.
Last October, Min H. Kao Department of Electrical Engineering and Computer Science (EECS) Assistant Professor Fnu Suya, his students, and their collaborators from the University of Florida published their discovery of the next big cybersecurity threat: Hardware-Model Logically Combined Attacks (HAMLOCKs).
“We uncovered a very powerful new attack strategy where a vulnerability in the hardware can interact with vulnerabilities in AI and ML software,” Suya said.
Individually, each component in the novel attack is harmless. The threat to users only arises if the right software is run on the right hardware, making the approach practically undetectable with current methods.

The discovery of HAMLOCKs is already making a splash worldwide; the team’s paper was recently accepted to Usenix Security 2026, one of the most exclusive and impactful cybersecurity conferences in the world.
Cisco Systems, Inc. (Cisco), an industry leader in networking and telecommunications with a branch in Knoxville, is keen to battle HAMLOCKs and isn’t content to wait until the conference. The company recently began developing AI-powered network analysis and traffic analysis tools, so defending against the newly discovered compound attack is a top priority.
“We’re excited to support Dr. Suya’s innovative research into HAMLOCK-style attacks—an approach that brings to light novel risks where hardware and software intersect in advanced AI systems,” said John White, director of the Advanced Security Initiatives Group at Cisco.

This September, Suya was awarded a $60,000 seed grant from AI TechX, UT’s initiative to spur AI innovation through industry partnerships, to collaborate with Cisco in investigating how custom hardware vulnerabilities might interact with various types of AI models.
“The AI TechX initiative represents a pivotal opportunity to help position Tennessee as a leader in responsible and secure AI adoption across industries,” White said. “At Cisco, we recognize that collaboration with academic researchers is critical to staying ahead of nation-state level threats, and we are proud to partner with the University of Tennessee to advance the frontiers of cybersecurity.”
Building a New Backdoor
In Trojan attacks against conventional software, users are tricked into installing malicious code wrapped in an innocent package.
Backdooring extends Trojan-style attacks to many types of ML software. Cybercriminals will release open source models or training data sets that appear normal, but when users harness them to train or refine ML algorithms, the resulting models include exploitable vulnerabilities.
“Let’s say you have an AI-based surveillance system on a building, and I’m not authorized to enter,” Suya said. “If I backdoor your model, then I can, for example, wear a certain pair of glasses and gain access.”
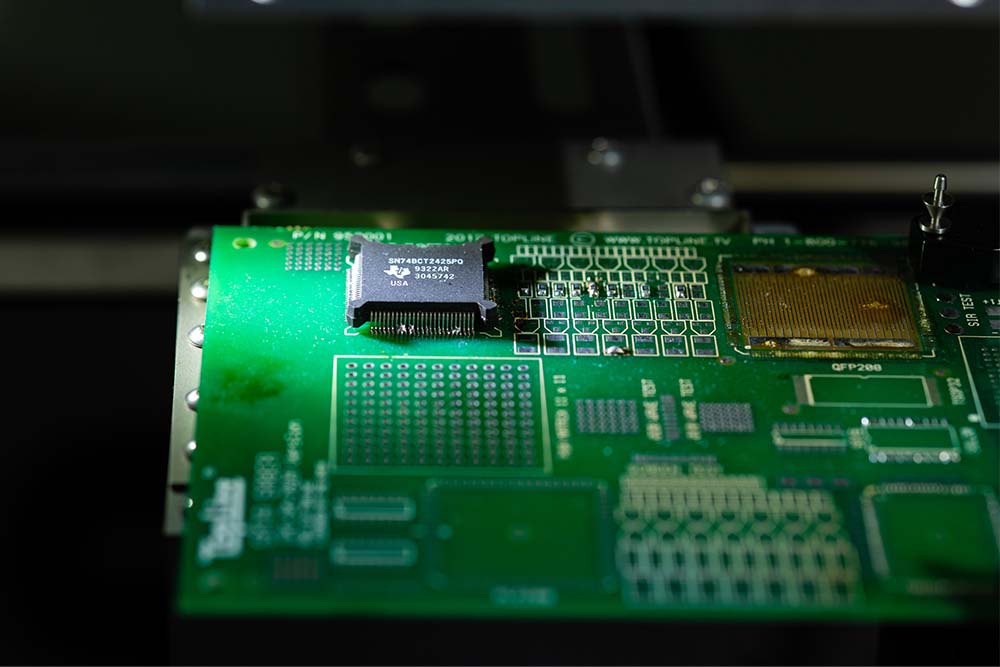
Such model Trojans can often be discovered by tracing errors backwards through the model, from erroneous result to poisoned origin. HAMLOCKs evade such detection by moving a few critical steps of the process onto the hardware. Since those important hallmarks of poisoned software aren’t present in the software anymore, they avoid being detected by existing sanitization tools.
Meanwhile, it’s alarmingly easy to implant those critical steps onto innocent-looking hardware. There is currently no certification process for AI-enhancing hardware; instead, most of the add-on devices that improve AI performance or efficiency are built by small groups with little to no oversight.
Suya’s team discovered a way to build lightweight hardware Trojans into these add-on devices. Running malicious code on such a compromised device triggers the hardware to build a backdoor into the final product, creating a compromised model that is not detectable with traditional methods.
“There is a ton of literature on how to check the hardware and software individually,” Suya said, “but there’s currently no way to check both.”
Impactful Cybersecurity Research
While academic research is what revealed the new cybersecurity threat, Cisco’s involvement is the key to making Suya’s results actionable.
“There’s so many things we can do with this new threat model. The key question is, what are the useful ones?” Suya said. “I have this cool research publication about a new threat, but for that to matter, I need insight and critique from people in the industry.”

Collaborating with Cisco’s researchers will give Suya’s team access to real-world data sets, which will be free from common assumptions made when academics generate test data, said Suya.
The industry researchers will also provide insight into how to translate scientific results into usable cybersecurity tools.
“We don’t want to just deliver one project; we want this to be an active research area,” said Suya. “Hopefully this is the start of a long collaboration with Cisco where we explore many topics together. Cisco is a great partner for cybersecurity work; I’m excited to see what general scientific insights and novelty we can bring to the field.”
Contact
Izzie Gall (egall4@utk.edu)
